Search
Search Results
-

-

-
Post-Quantum Cryptography 16th International Workshop, PQCrypto 2025, Taipei, Taiwan, April 8–10, 2025, Proceedings, Part I
The two-volume set LNCS 15577 + 15578 constitutes the proceedings of the 16th International Workshop on Post-Quantum Cryptography, PQCrypto 2025,...

-
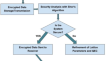
QuantumResist: integrating shor’s algorithm, lattice-based cryptography, and quantum error correction for enhanced secure communication in post-quantum cryptography
QuantumResist brings a new and improved way to secure communication in the quantum computing age with its use of lattice-based cryptography, quantum...
-
Post-Quantum Cryptography 16th International Workshop, PQCrypto 2025, Taipei, Taiwan, April 8–10, 2025, Proceedings, Part II
The two-volume set LNCS 15577 + 15578 constitutes the proceedings of the 16th International Workshop on Post-Quantum Cryptography, PQCrypto 2025,...

-
On Quantum Transition in Cryptography through the Lens of Bibliometrics
AbstractCryptography, which has a history going back many centuries, is currently experiencing a transition from the classical paradigm to a quantum...

-
Cryptography
Before the modern age, cryptography was only used for encryption which is to use a secret key to convert readable text (cleartext) to unintelligible...
-
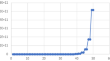
No Sum (NS) Sequence Based Post-Quantum Cryptography
Quantum computing is becoming a significant technology for addressing complex problems, including those in cryptography. Traditional cryptography now...
-
Multivariate Blind Signatures Revisited
In 2017, Petzoldt, Szepieniec, and Mohamed proposed a blind signature scheme, based on multivariate cryptography. This construction has been expanded...
-
The regular multivariate quadratic problem
In this work, we introduce a novel variant of the multivariate quadratic problem, which is at the core of one of the most promising post-quantum...

-
Securing the future: exploring post-quantum cryptography for authentication and user privacy in IoT devices
With the emergence of quantum computers, traditional cryptographic methods are vulnerable to attacks, emphasizing the need for post-quantum...

-
Post-Quantum Cryptography 15th International Workshop, PQCrypto 2024, Oxford, UK, June 12–14, 2024, Proceedings, Part I
The two-volume set LNCS 14771 and 14772 constitutes the refereed proceedings of the 15th International Workshop, PQCrypto 2024, held in Oxford, UK,...

-
Post-Quantum Cryptography 15th International Workshop, PQCrypto 2024, Oxford, UK, June 12–14, 2024, Proceedings, Part II
The two-volume set LNCS 14771 and 14772 constitutes the refereed proceedings of the 15th International Workshop, PQCrypto 2024, held in Oxford, UK,...

-
Exploring the landscape of post quantum cryptography: a bibliometric analysis of emerging trends and research impact
With the emergence of quantum computers, classical cryptography is facing significant challenges. Address this compelling problem, it is the need of...

-
An Effective Security Enhancement Scheme for Postquantum Cryptography Based Blockchain Networks in Cloud Computing
Lattice-based cryptography is widely embraced for its strong security and versatility, particularly in postquantum public key (PK) systems. The...

-
Integrating code-based post-quantum cryptography into SSL TLS protocols through an interoperable hybrid framework
The advancement of quantum computing creates a big threat to classical cryptographic protocols, including TLS, which is responsible for secure...

-
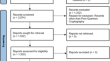
Analyzing the research impact in post quantum cryptography through scientometric evaluation
The accelerated pace of development in the Field of Quantum Computing is very alarming for many of the presently used cryptographic algorithms such...
-
A New Multivariate Primitive from CCZ Equivalence
Multivariate cryptography is one of the candidates for post-quantum cryptography. Multivariate schemes are usually constructed by applying two secret...
-
Algebraic Cryptanalysis and Countermeasures of Lightweight Signature Scheme Based on Multivariate Quadratic Polynomials
Multivariate Public Key Cryptography (MPKC) is a promising candidate for Post Quantum Cryptography (PQC) that ensures data security, information...
-
Post-Quantum Cryptography 14th International Workshop, PQCrypto 2023, College Park, MD, USA, August 16–18, 2023, Proceedings
This book constitutes the refereed proceedings of the 14th International Workshop on Post-Quantum Cryptography, PQCrypto 2022, held in College Park,...

