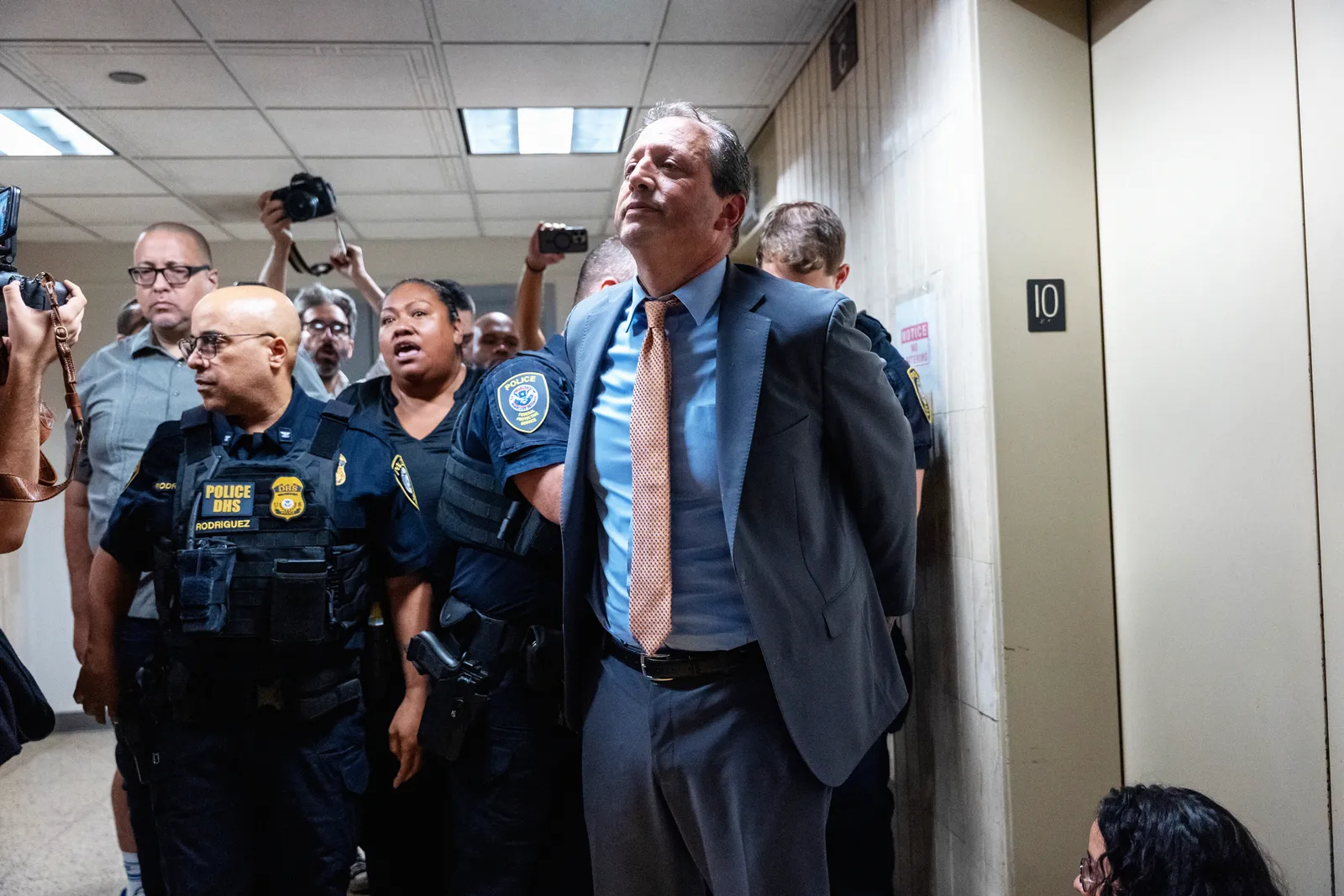Security

Infections
A New Attack Lets Hackers Steal 2-Factor Authentication Codes From Android Phones
The malicious app required to make a “Pixnapping” attack work requires no permissions.

Buying Guide
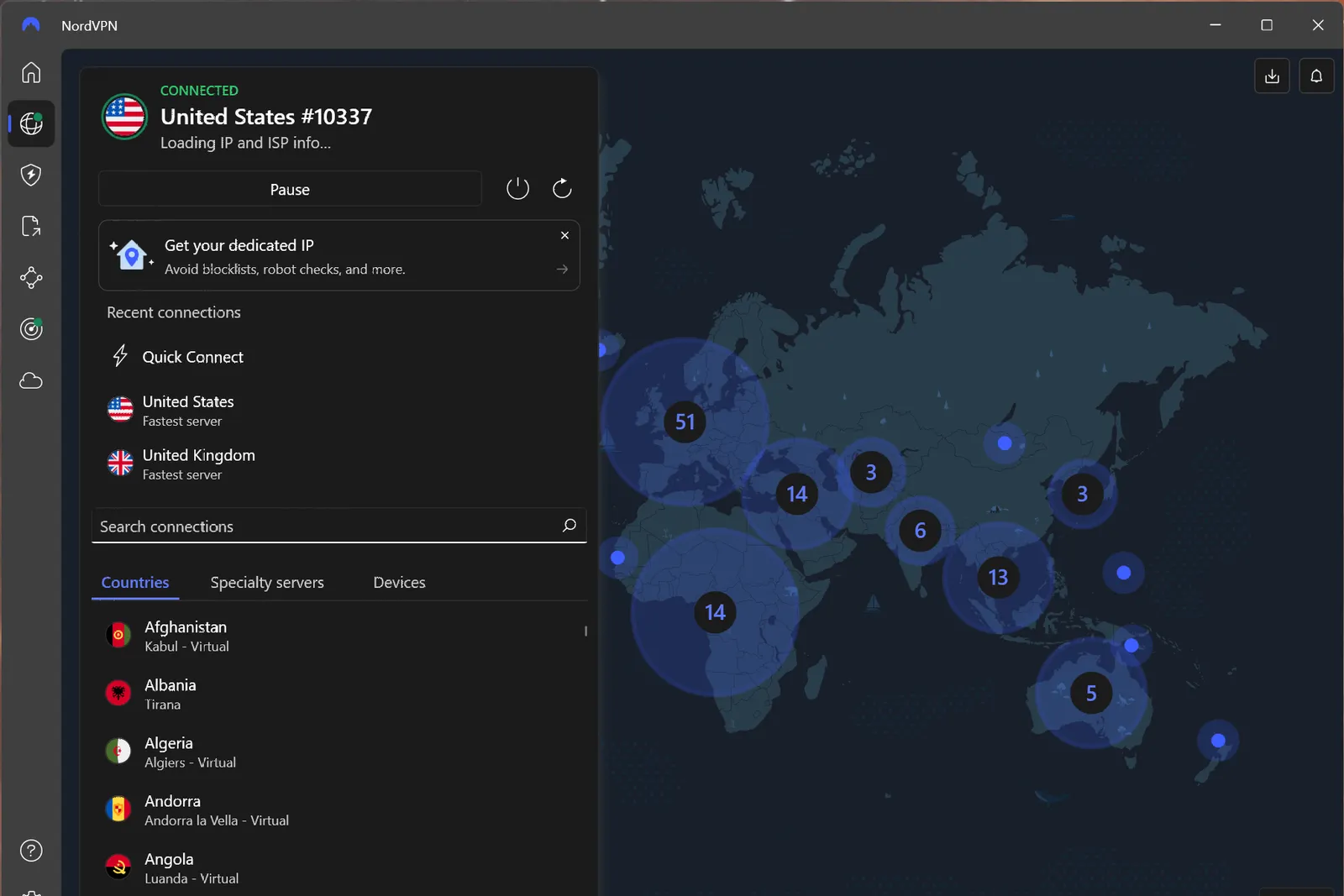
The Best VPNs for iPhone

Satellites Are Leaking the World’s Secrets
With just $800 in basic equipment, researchers found a stunning variety of data—including thousands of T-Mobile users’ calls and texts and even US military communications—sent by satellites unencrypted.

Happy Gilmore Producer Buys Spyware Maker NSO Group
Plus: US government cybersecurity staffers get reassigned to do immigration work, a hack exposes sensitive age-verification data of Discord users, and more.

Apple Announces $2 Million Bug Bounty Reward for the Most Dangerous Exploits
With the mercenary spyware industry booming, Apple VP Ivan Krstić tells WIRED that the company is also offering bonuses that could bring the max total reward for iPhone exploits to $5 million.

Vibe Coding Is the New Open Source—in the Worst Way Possible
As developers increasingly lean on AI-generated code to build out their software—as they have with open source in the past—they risk introducing critical security failures along the way.

Apple and Google Pull ICE-Tracking Apps, Bowing to DOJ Pressure
Plus: China sentences scam bosses to death, Europe is ramping up its plans to build a “drone wall” to protect against Russian airspace violations, and more.

ICE Wants to Build Out a 24/7 Social Media Surveillance Team
Documents show that ICE plans to hire dozens of contractors to scan X, Facebook, TikTok, and other platforms to target people for deportation.

Tile Tracking Tags Can Be Exploited by Tech-Savvy Stalkers, Researchers Say
A team of researchers found that, by not encrypting the data broadcast by Tile tags, users could be vulnerable to having their location information exposed to malicious actors.

An App Used to Dox Charlie Kirk Critics Doxed Its Own Users Instead
Plus: A ransomeware gang steals data on 8,000 preschoolers, Microsoft blocks Israel’s military from using its cloud for surveillance, call-recording app Neon hits pause over security holes, and more.

How to Use Passkeys With Google Password Manager
Google can create and manage passkeys from your browser, but the process is more involved than it suggests.

How to Use a Password Manager to Share Your Logins After You Die
Your logins will live on after you pass on. Make sure they end up in the right hands.

How to Set Up and Use a Burner Phone
Obtaining and using a true burner phone is hard—but not impossible. Here are the steps you need to take to protect your mobile communications based on the risks you face.

The Password Managers You Should Use Instead of Your Browser
Keep your logins locked down with our favorite password management apps for PC, Mac, Android, iPhone, and web browsers.

North Korean Scammers Are Doing Architectural Design Now
New research shows that North Koreans appear to be trying to trick US companies into hiring them to develop architectural designs using fake profiles, résumés, and Social Security numbers.

Apple Took Down These ICE-Tracking Apps. The Developers Aren't Giving Up
“We are going to do everything in our power to fight this,” says ICEBlock developer Joshua Aaron after Apple removed his app from the App Store.

Google’s Latest AI Ransomware Defense Only Goes So Far
Google has launched a new AI-based protection in Drive for desktop that can shut down an attack before it spreads—but its benefits have their limits.

How a Travel YouTuber Captured Nepal’s Revolution for the World
Harry Jackson went into Kathmandu as a tourist. He ended up being one of the main international sources of news on Nepal’s Gen Z protests.
Latest

Security Roundup